Trends Shaping the Cybersecurity Landscape in 2022
According to Forrester, “The combination of data and machines could fuel either techno-optimistic utopia (happier, healthier lives for all) or totalitarian dystopia (corporations and governments using personal data to extract oligopolistic rents and control people).” A range of mitigating factors and trends are shaping this cybersecurity landscape.
There’s no question that cybersecurity is advancing faster than anyone in recent history could have predicted. The point we are at right now was unfathomable just ten years ago, which raises the question, what will the landscape look like even a year from now?
Artificial Intelligence (AI) and connected devices are now part of our collective reality. The smarter our devices become, the more we can accomplish, and innovators are constantly discovering new ways to entice, amaze, and expand those capabilities.
As these technologies mature and become more accessible and ubiquitous, the number of endpoints has multiplied exponentially. Cheaper or fast-to-market devices often lack security features to protect them from unauthorized access, creating a perfect storm of vulnerability that, if unchecked, could threaten the security of everything we touch.
Download our free eBook, The Top 16 Cyberthreats of 2022.
From our personal lives to vital infrastructure, it’s all at risk. As a result, cybersecurity specialists face a never-ending uphill battle as they struggle to stay ahead of innovation amid a global cyber talent shortage and a swath of unknowns on the horizon. Zyston’s President and CEO, Craig Stamm, understands the need to act swiftly and continues to look forward, ensuring we are always several steps ahead of the threat environment and going ‘Beyond the Alert.’
What Lies Ahead?
Assessing the future of cybersecurity requires deep insight—not just into the threat environment and what’s at stake, but also into the human landscape, how we work, the technology we use, and the challenges of these scenarios.
The FBI reported an unprecedented increase in cybersecurity incidents in the past year, and it’s estimated that the cost of cybercrime is on track to exceed $6.1 trillion by the end of 2022.
A summary of trends shaping the cybersecurity landscape:
Remote work/work from home
The pandemic forced businesses to pivot operations to accommodate work from home and distributed teams. This situation, while necessary to support business continuity, increased vulnerabilities through unsecured networks, shared devices, and a lowered threshold for enforcing security policies. BusinessWire reports that 81% of global organizations have experienced increased cyberthreats during the pandemic. Endpoints multiplied overnight, pushing already strained resources to the max and exposing networks, individuals, and company data to cyberthreats at scale.
The data economy
Data is the primary focus of most malicious cyber-attacks. Whether hackers seek to steal data or manipulate it to deceive the public interest, the focus must look beyond data confidentiality, integrity, and availability. Consensus has it that we simply don’t yet have the right controls in place to safeguard data integrity, and the evidence to support this idea is everywhere.
Consumers don’t trust companies to keep their data safe. They might choose one company over another if they were to feel confident that their data was safe and protected, but most firms won’t be able to deliver this because of a few mitigating factors.
First, marketing and CX teams do not generally work closely with data security experts to ensure procedural security. Their understanding of data stewardship is vastly different, making it challenging to align both teams around shared outcomes.
The issue of ethical use of data is a hot-button issue too, with major companies like Twitter racking up millions of dollars in fines for misappropriation of user data for ad targeting, further eroding public trust. Our data is used by companies and even governments to watch, record, predict, and sell, and it’s no secret who’s doing it or why.
Automation
Today’s automation consumes massive amounts of data to initiate actions and decisions with little to no human involvement, underscoring the need to protect the integrity of that data. Malicious actors have been quick to exploit organizations that have invested poorly in this area, gaining access to autonomous systems to wreak chaos and potentially destroy lives and businesses in the process.
One notable example of this is a recent experiment on Tesla, where Israeli researchers discovered that flashing a couple of frames of a stop sign onto a connected billboard or projecting an image of a pedestrian for a split second was enough to stop the car. The researchers were quick to point out that should a hacker take over a connected billboard in this manner, they could easily cause major disruption, traffic jams, or accidents on the roads with little evidence to explain what happened.
Thousands of new IoT devices
IoT is essential to healthcare, manufacturing, autonomous vehicles, logistics, and more. With people spending more time at home, IoT has also exploded in the consumer realm. The market has grown by $250 billion since 2020 and continues to gain ground. Device security is imperative, as a breach could be a life-or-death situation.
Artificial Intelligence (AI)
AI supports consumers from predicting search intent to serving up programming suggestions on Netflix and optimizing home comfort through various connected and voice-controlled devices. Combined with machine learning, it can create a highly personalized environment constructed of your personal data—data you’ve given freely as you understand the benefits it delivers. It is also a crucial tool in terms of combatting cybercrime and staying ahead of attacks. Companies with no security AI and automation averaged a cost of $6.71M per breach, whereas an organization with a fully deployed system saw costs averaging $2.90M.
However, this can be a double-edged sword. We allow machines access to our data, but without a clear understanding of how technology vendors use that data beyond transactions, users are exposed to considerable risk from data misappropriation, malicious advertising, or manipulative contexts designed to profit the vendor.
AI’s ability to mimic human behaviors and responses makes it much easier for criminals to trick people into giving up credentials, payment information, and even biometric data. There is even talk about how companies can turn AI apps into judicial “people” to give them control of LLCs, arguably the next frontier of AI. AI arbitrage is already used in the securities sector to automate trading, so it would seem that AI personage is the logical next step. Would this place a company “led” by an AI beyond the scope of data regulators?
Ultimately, the writing is on the wall. The combination of AI and the data economy will push us to extremes, forcing mistakes on a scale not easily imagined by today’s standards and keeping security experts and regulators on their toes as they attempt to anticipate and mitigate the coming storm.
Ransomware
Some of the most destructive ransomware attacks have targeted vital infrastructure and sent entire geographical regions into chaos, putting lives and livelihoods at stake. Backup and recovery plans are essential strategies, but humans are often the weakest link. Dynamic monitoring is critical, but awareness, education, and strong security policies are the best defense.
People, Process, Technology
At Zyston, we know that people are one of the most crucial aspects of a cybersecurity program. Looking ahead, the human element will undoubtedly become even more critical as organizations struggle to attract and retain qualified cyber talent.
Managed solutions are cost-effective, but a more tailored approach is required when the goal is to mature and strengthen the security program. With a dedicated program manager to bridge the communication gap between managed services and stakeholders within the organization, companies are assured of an approach that considers their unique needs, challenges, and risk environment.
To learn more, download our free eBook, The Top 16 Cyberthreats of 2022.
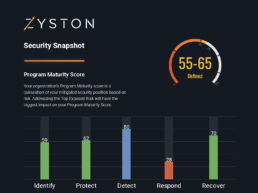
CyberCast Security Reporting
Security reporting that speaks business
Zyston CyberCAST brings the world of cybersecurity metrics up out of the weeds and into the hands of executive decision makers so nothing gets lost in translation. With CyberCAST, your organization gets clear visibility on security risks and also how your organization scores against your industry peers.




















