How to Develop a Cybersecurity Strategy?
Nowadays, businesses have concluded that they need a comprehensive cybersecurity strategy to defend themselves and their information from cyber-attacks. A well-designed cybersecurity program should cover the entire spectrum of information security, from adequate physical controls to technical safeguards to user behavior, and be tailored to an organization’s specific needs.
Here, we will discuss what a cybersecurity program is and the steps reliable cybersecurity companies follow to create a successful cybersecurity strategy.
What Is a Cybersecurity Program?

A cybersecurity program refers to a set of documented information security policies, procedures, guidelines, and standards implemented within an organization.
To guarantee that your clients and organization’s private information remains secure, a robust security program must be developed with effective management practices and controls. This program should serve as a guide to successfully manage security and avoid breaches of confidentiality, integrity, and availability of sensitive data.
Steps of a Cybersecurity Strategy
Step #1: Conduct a Security Risk Assessment
Organizations perform IT enterprise security risk assessments to evaluate, recognize, and adjust their security framework. This is essential for obtaining the organization’s management support, allocating resources, and implementing effective security solutions.
Partnering with a cybersecurity company to conduct a thorough risk assessment for enterprise security can also aid in evaluating the importance of different types of data produced and stored throughout the company.
Some things to take into consideration are:
- Identify assets
- Identify threats and vulnerabilities
- Analyze risks to assets
- Select security controls
Take free CyberCAST Snapshot risk assessment with Zyston to see where your business risks are most prevalanet.
Step #2: Define your Security Goals
To implement a proactive cybersecurity program for the entire organization, aligning the strategy with the company’s business goals is important. Therefore, the first step is establishing the business goals before beginning the implementation process. If you are still unsure of the goals you want to achieve, working with a cybersecurity expert can help you see them more clearly after the risk assessment.
Step #3: Evaluate your Current Technology
It is important to comprehensively understand the tools and technologies used within the organization before designing a cybersecurity strategy. An evaluation should focus on both hardware and software. A cybersecurity expert can you assess the operating systems, cloud systems, and other tools used to store data. Nowadays, even AI can be considered helpful for any cybersecurity strategy.
Step #4: Design a Security Policy
Organizations are advised to develop and maintain a comprehensive security policy. A security policy created by a trusted MSSP should include all essential details, such as the document’s purpose, the scope of coverage, definitions of key terms used, implementation objectives, etc.
Step #5: Create a Risk Management Plan
Including a risk management plan as part of the cybersecurity strategy is essential. A cybersecurity company should be able to develop a plan that evaluates possible risks that could affect the organization. By anticipating and analyzing potential risks, this plan helps business take action to prevent any negative impact on the company before they happen.
Things to take into consideration are:
- Data Privacy Policy: Offers governance to ensure corporate data is correctly managed and secured.
- Retention Policy: Specifies where, how long, and how different categories of company data should be stored or archived.
- Data Protection Policy: In this policy, the company outlines how it manages the personal information of its clients, suppliers, workers, and other third parties.
- Incident Response Plan: This plan defines the duties and steps that must be taken to ensure a prompt, efficient, and organized response to security incidents.
Step #6: Implement Your Security Strategy
Businesses need to implement a comprehensive cybersecurity strategy throughout the organization. This process should incorporate the risk management plan to ensure that all data is properly protected and the security infrastructure is up-to-date.
Step #7: Evaluate Your Strategy
It is also important that your cybersecurity partners reviews the security strategy periodically. This can be done through audits, penetration tests, assessments, surveys, and other methods to ensure that the security measures are effective and that any potential vulnerabilities have been identified.
Want to Know How to Solve Cybersecurity Issues?
Having a cybersecurity strategy in your company is a must! It will help you protect your data and remediate any potential issues. However, having a plan in place is only the first step. You must also consider who to partner with to get a cybersecurity solution that meets your needs.
You should consider getting the help of a managed security services provider (MSSP). An MSSP is a third party specializing in managing and monitoring cybersecurity threats. At Zyston, we understand the importance of security and provide our clients with a comprehensive cybersecurity program tailored to their specific needs.
With Zyston’s managed security services, you can be sure that your data and IT infrastructure are always protected. So get in touch and let our expert team assist you!
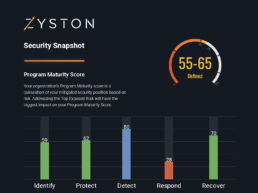
CyberCast Security Reporting
Security reporting that speaks business
Zyston CyberCAST brings the world of cybersecurity metrics up out of the weeds and into the hands of executive decision makers so nothing gets lost in translation. With CyberCAST, your organization gets clear visibility on security risks and also how your organization scores against your industry peers.




















