In today’s rapidly evolving digital landscape, cybersecurity threats have become increasingly sophisticated and persistent. This article delves into the latest trends in cyberattacks, providing insights into how these threats have escalated, with global cyberattacks increasing by 38% in 2023. As a trusted leader in cybersecurity, Zyston brings a wealth of expertise and experience to this discussion, offering you actionable strategies to safeguard your organization.
Continuous Threat Exposure Management (CTEM) is a proactive and dynamic approach to cybersecurity that involves the continuous identification, assessment, and mitigation of potential threats to an organization’s digital infrastructure. Unlike traditional cybersecurity measures that often rely on periodic assessments and updates, CTEM emphasizes real-time monitoring and immediate response to emerging threats. This methodology ensures that organizations are always a step ahead of cyber adversaries, rather than reacting to breaches after they occur.
One of the core principles of CTEM is continuous monitoring. This involves the use of advanced tools and technologies to keep a constant watch on the organization’s network, systems, and data. Continuous monitoring enables the detection of suspicious activities and potential threats as they happen, allowing for rapid response and mitigation. This proactive stance is crucial in the current threat landscape, where new vulnerabilities and attack vectors emerge daily.
Threat intelligence is integral to CTEM. By leveraging threat intelligence, organizations can gain insights into the latest tactics, techniques, and procedures (TTPs) used by cyber adversaries. This information is critical for understanding the threat landscape and adapting security measures accordingly. Threat intelligence helps in identifying potential threats before they materialize into actual attacks, thereby enhancing the organization’s ability to defend against them.
CTEM involves a comprehensive approach to vulnerability management. Traditional vulnerability management often relies on scheduled scans and updates, which may leave gaps in security. In contrast, CTEM requires continuous scanning and assessment of vulnerabilities. This means regularly identifying and evaluating vulnerabilities in the organization’s systems and applications and prioritizing remediation efforts based on the potential impact and likelihood of exploitation. By addressing vulnerabilities promptly, organizations can significantly reduce their attack surface and enhance their overall security posture.
Integration of various security controls and practices into a cohesive framework is crucial for CTEM. This includes Managed Detection and Response (MDR), Security Information and Event Management (SIEM), and Penetration Testing, among others. By integrating these components, organizations can ensure a holistic and coordinated approach to threat exposure management. For instance, MDR provides real-time threat detection and response capabilities, while SIEM offers centralized visibility and analysis of security events. Penetration testing simulates cyberattacks to identify weaknesses and validate the effectiveness of security measures.
CTEM values the importance of human expertise. Skilled cybersecurity professionals play a vital role in continuous threat exposure management. They bring the necessary knowledge and experience to interpret threat intelligence, conduct risk assessments, and implement effective security strategies. By combining advanced technologies with human expertise, organizations can achieve a higher level of cyber resilience and be better prepared to face the challenges posed by the evolving threat landscape.
In conclusion, Continuous Threat Exposure Management is a comprehensive and proactive approach to cybersecurity. By continuously monitoring for threats, leveraging threat intelligence, managing vulnerabilities, and integrating various security controls, organizations can effectively mitigate risks and enhance their cyber resilience. Adopting CTEM allows organizations to stay ahead of cyber adversaries and protect their digital assets in an ever-changing threat environment. As a leader in cybersecurity, Zyston is committed to helping organizations implement and maintain robust CTEM practices to ensure their long-term security and success.
By reading this article and adopting Continuous Threat Exposure Management (CTEM), organizations can proactively address these evolving threats and enhance their resilience against cyberattacks.
Understanding Continuous Threat Exposure Management
Continuous Threat Exposure Management (CTEM) is a proactive and ongoing process of identifying, assessing, and mitigating cybersecurity threats. Unlike traditional cybersecurity measures that rely on periodic assessments, CTEM emphasizes continuous monitoring and real-time responses to the ever-evolving threat landscape. Adopting CTEM offers significant benefits, including improved threat detection and response times, reduced risk of cyberattacks and data breaches, and enhanced overall security posture and compliance with regulations.
Gartner has highlighted a significant issue with many Managed Security Service Providers (MSSPs): they often function like a “black box,” offering limited visibility into their operations and failing to share crucial data with clients. This lack of transparency can hinder organizations from integrating critical security insights into their broader cybersecurity strategies. Without CTEM, these MSSPs may not effectively identify or respond to emerging threats, leaving clients vulnerable to sophisticated cyberattacks.
Why Continuous Threat Exposure Management is Crucial
1. Evolving Threat Landscape
Cyber threats are not static; they evolve rapidly as attackers develop new techniques to bypass existing security measures. Continuous Threat Exposure Management allows organizations to stay ahead of these advancing threats by constantly monitoring and updating their security protocols. This agility is essential in an environment where new vulnerabilities can be discovered and exploited within hours.
2. Proactive Risk Mitigation
Traditional cybersecurity strategies often focus on responding to incidents after they have occurred. In contrast, CTEM emphasizes proactive risk mitigation by identifying potential vulnerabilities before they can be exploited. This proactive stance significantly reduces the likelihood of successful attacks, minimizing the potential damage and associated costs. According to a recent study, organizations with proactive threat detection and response capabilities reduce their average breach costs by 30% compared to those with reactive approaches.
3. Enhanced Incident Response
When a security breach does occur, a well-implemented CTEM strategy ensures that organizations can respond swiftly and effectively. By continuously monitoring for threats, companies can detect breaches in their early stages and take immediate action to contain and remediate the issue. This rapid response capability is crucial in limiting the impact of cyber incidents.
4. Compliance and Regulatory Requirements
Many industries are subject to stringent cybersecurity regulations and standards. Continuous Threat Exposure Management helps organizations maintain compliance with these requirements by providing a framework for ongoing security assessment and improvement. This not only helps avoid legal penalties but also builds trust with clients and stakeholders.
5. Cost Efficiency
Data from the Ponemon Institute reveals that organizations with robust incident response capabilities can reduce the cost of a data breach by up to $1.2 million. While implementing CTEM requires an investment in advanced monitoring tools and skilled personnel, it is ultimately more cost-effective than dealing with the aftermath of a major security breach. The costs associated with data breaches—including financial loss, reputational damage, and regulatory fines—can be staggering. By preventing breaches before they occur, CTEM provides a significant return on investment. IBM’s Cost of a Data Breach Report 2023 indicated that organizations with mature CTEM practices saw a 26% reduction in breach costs compared to those without such measures.
Key Components of CTEM
Continuous Threat Exposure Management (CTEM) is essential for maintaining a robust cybersecurity posture in an increasingly complex digital environment. This approach integrates multiple security measures to provide comprehensive protection against evolving threats. Each component of CTEM plays a critical role in safeguarding an organization’s digital infrastructure by ensuring continuous monitoring, threat detection, and response capabilities. Understanding these components helps organizations implement effective security strategies, mitigate risks, and enhance their overall cyber resilience.
Managed Detection and Response (MDR)
Explain MDR: MDR is a service that combines advanced technology with human expertise to detect and respond to cybersecurity threats. By integrating with other security measures, MDR provides comprehensive protection, ensuring that potential threats are identified and addressed in real-time.
Describe Zyston’s MDR Services:
- 24/7 Monitoring: Continuous surveillance of networks and systems to detect suspicious activities.
- Advanced Threat Detection: Utilizing advanced analytics and machine learning to identify potential threats.
- Incident Response: Providing immediate action to mitigate and resolve security incidents.
Real-World Application: For example, a manufacturing company used Zyston’s MDR services to detect and respond to a potential ransomware attack, preventing significant downtime and financial loss.
Vulnerability Management
Define Vulnerability Management: Vulnerability management is the process of identifying, evaluating, and mitigating security vulnerabilities. Its primary role is to prevent the exploitation of known weaknesses.
Vulnerability Management Process:
- Identification: Regular scanning of systems and networks to find vulnerabilities.
- Evaluation: Assessing the severity and potential impact of identified vulnerabilities.
- Remediation: Implementing fixes and patches to address vulnerabilities.
- Verification: Ensuring that vulnerabilities have been successfully mitigated.
Zyston’s Approach:
- Comprehensive Scanning: Utilizing advanced tools to perform thorough scans.
- Risk Assessment: Prioritizing vulnerabilities based on potential impact and likelihood of exploitation.
- Patch Management: Coordinating with IT teams to deploy patches and updates promptly.
Managed SIEM
Define Managed SIEM: SIEM systems aggregate and analyze security data from various sources, providing actionable insights and enhancing threat detection.
Benefits of SIEM:
- Enhanced Visibility: Providing a centralized view of security events and activities.
- Improved Threat Detection: Correlating data from multiple sources to identify sophisticated threats.
- Streamlined Compliance: Assisting in meeting regulatory requirements by maintaining detailed logs and reports.
Zyston’s Managed SIEM Services:
- Implementation: Setting up and configuring SIEM systems tailored to client needs.
- Management: Ongoing monitoring, maintenance, and tuning of SIEM systems to ensure optimal performance.
- Analysis and Reporting: Generating detailed reports and alerts to keep clients informed of their security posture.
Ransomware Detect and Respond (RDR)
Define Ransomware Detect and Respond: RDR is a proactive approach to identifying and mitigating ransomware threats before they cause damage. Early detection and rapid response are crucial.
RDR Process:
- Detection: Monitoring systems for signs of ransomware activity, such as unusual file modifications or encryption attempts.
- Response: Taking immediate action to isolate affected systems, remove ransomware, and restore data from backups.
Zyston’s RDR Services:
- Proactive Monitoring: Utilizing advanced tools to detect ransomware behaviors.
- Incident Response: Providing rapid response teams to contain and eradicate ransomware threats.
- Recovery and Remediation: Assisting clients in recovering data and implementing measures to prevent future attacks.
Penetration Testing
Define Penetration Testing: Penetration testing simulates cyberattacks to identify security weaknesses, validating the effectiveness of security measures.
Zyston’s Methodology:
- Planning: Defining the scope and objectives of the penetration test.
- Execution: Conducting simulated attacks using various techniques to identify vulnerabilities.
- Reporting: Documenting findings and providing recommendations for remediation.
- Remediation: Assisting clients in addressing identified vulnerabilities.
Zyston’s Expertise:
- Experienced Testers: Utilizing skilled professionals with deep knowledge of the latest attack techniques.
- Comprehensive Approach: Covering a wide range of attack vectors, including network, application, and physical security.
- Actionable Insights: Providing detailed reports and guidance to enhance clients’ security postures.
Risk Assessments
Define Risk Assessments: Risk assessments involve identifying, evaluating, and prioritizing risks to an organization’s assets. A systematic approach is crucial for effective risk management and mitigation.
Risk Assessment Process:
- Identification: Cataloging potential risks to the organization’s assets.
- Evaluation: Assessing the likelihood and impact of each identified risk.
- Prioritization: Ranking risks based on their potential impact and likelihood of occurrence.
- Mitigation: Developing and implementing strategies to address high-priority risks.
Zyston’s Risk Assessment Services:
- Comprehensive Evaluations: Conducting thorough assessments of clients’ security environments.
- Custom Recommendations: Providing tailored recommendations to address identified risks.
- Ongoing Support: Offering continuous support to ensure effective risk management.
Human Capital Services
Importance of Human Capital in Cybersecurity: Skilled cybersecurity professionals are crucial for effective continuous threat exposure management. Human expertise complements technological solutions, enhancing overall security effectiveness.
Zyston’s Human Capital Services:
- Talent Acquisition: Sourcing and placing top cybersecurity talent at every level, from entry-level to executive positions.
- Training and Development: Providing ongoing training and development programs to keep cybersecurity professionals up-to-date with the latest trends and techniques.
- Consulting Services: Offering expert consulting services to help organizations optimize their cybersecurity strategies and operations.
Zyston’s Approach to Continuous Threat Exposure Management
According to a recent study, organizations with proactive threat detection and response capabilities reduce their average breach costs by 30% compared to those with reactive approaches.
Zyston’s CyberCAST 3.0 revolutionizes continuous threat exposure management by providing a comprehensive suite of tools and methodologies. At its core, CyberCAST offers a platform designed to measure, optimize, and communicate cybersecurity risks within organizations. CyberCAST delivers invaluable insights into your susceptibility to threats. With the AI Assist Assessment, we prioritize efficiency, offering the quickest time-to-value in the industry. This translates to significant reductions in time and labor traditionally invested in assessments, ensuring comprehensive protection across all facets of your business.
Our approach to continuous threat exposure management encompasses various key components:
- Continuous NIST 2.0 program assessing
- Continuous Attack Surface Management
- Continuous Attack Simulations (Penetration Testing)
- Continuous Offensive Security Testing (Attack Surface)
- Continuous Cloud Security Compliance Scanning
By seamlessly integrating these elements, Zyston empowers organizations to proactively identify, mitigate, and adapt to evolving cyber threats, safeguarding their operations and assets effectively.
Conclusion
In an era where cyber threats are a constant and evolving challenge, Continuous Threat Exposure Management is not just a luxury—it’s a necessity. By preventing breaches before they occur, CTEM provides a significant return on investment. IBM’s Cost of a Data Breach Report 2023 indicated that organizations with mature CTEM practices saw a 26% reduction in breach costs compared to those without such measures.
At Zyston LLC, we are dedicated to providing our clients with the tools, knowledge, and support they need to protect their digital assets in this dynamic threat landscape. By embracing CTEM, organizations can defend against current threats and anticipate and mitigate future risks, ensuring their long-term security and success.
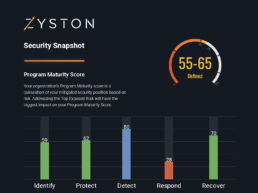
CyberCast Security Reporting
Security reporting that speaks business
Zyston CyberCAST brings the world of cybersecurity metrics up out of the weeds and into the hands of executive decision makers so nothing gets lost in translation. With CyberCAST, your organization gets clear visibility on security risks and also how your organization scores against your industry peers.




















