The Future of Cybersecurity
Introduction
Forrester states, “The combination of data and machines could fuel either techno-optimistic utopia (happier, healthier lives for all) or totalitarian dystopia (corporations and governments using personal data to extract oligopolistic rents and control people).”
The past five years have seen a plethora of new technologies transforming the way we do business and go about our day-to-day lives, and with the current pace of innovation, it seems we can expect more of the same in the near future. Data and machines have combined to mediate and enhance user experiences with voice interfaces, virtual and augmented reality, and predictive search all becoming integrated with everyday technologies.
Attackers have an asymmetric advantage over defenders within cyberspace, as trialing new technologies could leave defenders vulnerable, but a lack of innovation will subsequently leave them lagging behind.
What does this mean for Cybersecurity?
As the digital age propels forward, so does the risk of cybercrime. With technology developing and expanding at such a rapid rate there are increasingly more opportunities for hackers to expose businesses and individuals. However, the potential to proactively seek out cybercrime and protect against it has also increased. With the right tools and support your digital assets can continue to be secure as the world pursues its journey of innovation.
Liabilities for Companies
According to CyberCrime Magazine 60% of small companies go out of business within six months of falling victim to a data breach or cyber attack, with the average cost of a single breach hovering around $3.62 million.
With new technologies and advances, regulations tend to follow closely behind seeking out protective measures. If your business is not following the rules or has blind spots that result in a security breach the fallout could be devastating.
In June of 2021, LinkedIn was victim to a data breach that affected 92% of the platform’s users (over 700 million people), demonstrating that even high-tech companies have weaknesses they might not be aware of. One of the most expensive breaches cost Epsilon around $4 billion, when hackers stole client data from big brands such as Target, Best Buy and JP Morgan Chase.
On April 4th 2022 the US Department of State announced the new Bureau of Cyberspace and Digital Policy (CDP). CDP will focus on cyberspace, digital technologies, and digital policy, possibly establishing nationwide, up-to-date security regulations. In addition, at least seventeen states put general artificial intelligence bills or resolutions in place. Whilst there may not be universally set standards, staying in the know about your own cybersecurity, the rules of where you operate and the wider cyber landscape is crucial to protecting your company.
Consumer Trust
Forrester suggests that attitudes about privacy are already dire: according to the Analytics Consumer Technographics® Benchmark Survey, Part 2, 2020, 24% of US and UK online adults, 26% of German online adults, and 28% of French online adults don’t trust any company to keep their personal information safe. Ensuring privacy and security for consumers can be leveraged as a competitive advantage under the right circumstances. Internally, marketing teams must be better versed in consumer data risks and there should be alignment between marketing and security departments. Firms must focus on their own data ethics instead of relying solely on regulators. Externally, digital identities need to become less fragmented and more verifiable to build up trust from users.
Data Integrity
Data integrity is at the heart of the issue for cybersecurity as confidentiality, and availability has been focused on heavily by CISOs in the last decade. The data economy relies on analytics, automation and insights to inform decision-making with little to no human involvement, compromised data can lead to bad decisions. Autonomous systems assume the integrity of the data they receive, and hackers who can track down organizations who have not invested in safeguarding their data will attack this soft target.
Forrester’s Orwellian Data Cycle demonstrates the importance of data safety at each stage in the process, as well as highlighting how easy it is to manipulate. Businesses have rushed to extract value at each phase, placing enormous trust in the data they are fed. Poisoning this data will become a primary motivation for threat actors, reducing the efficacy of marketing campaigns, customer personas, and ultimately to brand destruction.
AI + The Data Economy
Artificial Intelligence has the ability to greatly benefit society and make people’s lives more comfortable and sustainable. This type of technology has unmatched potential in industries such as healthcare and is reducing the risk of human error across the board.
Market and Markets report that the artificial intelligence in the cybersecurity market is projected to reach USD 38.2 billion by 2026 from USD 8.8 billion in 2019, at the highest CAGR of 23.3%. Major drivers for this are the growing adoption of IoT and the increasing number of connected devices, rising instances of cyber threat, growing concerns of data privacy, and increasingly vulnerable Wi-Fi networks.
The combination of AI and the data economy will propel us further into the unknown of the cyberworld. There is more personal information available now than ever before, and this will continue to multiply as IoT expands the realms of cyberspace. Companies will be held accountable for ‘faking’ data security and antitrust organizations will begin to break up or investigate mergers and acquisitions that involve large quantities of data sharing.
The reality of AI personhood in the future is not far-fetched, and governing this change is difficult until we have the means to start to build reactive regulations. As AI technology continues to become more accessible and intelligent, there is a growing risk of malicious actors being able to generate fake text from fake people to automate and weaponize online chat interactions and facilitate fraud. Cybersecurity solutions need to be able to protect against such threats as we enter this phase of artificial intelligence.
People, Processes, + Technology as the Solution
However, it’s not all doom and gloom, whilst we know that cyberthreats will continue to evolve there are core principles and systems we can have in place to help mitigate these threats moving forward.
People
Having the right team of experts in place, whether it be internal or external, is at the heart of protecting your business from the ever-changing threat environment. Dedicated professionals who keep up to date with cybercrime and the digital landscape must be integrated into any company’s strategic discussions.
Technology alone will not be sufficient to provide protection, you need dedicated people with expertise, training, and knowledge to oversee your cybersecurity.
Processes
Ensuring protocols are being followed and there is regular updating of cybersecurity practices within an organization is key to not being left behind or having large blind spots when it comes to digital security.
Technology
When it comes to defending against new innovations in malicious threats you have to have the right technology in place to protect your business. Investing in the right tools, and knowing what those are, is paramount to keeping data secure and minimizing risks.
So Where Should You Start To Better Protect Your Business?
A cybersecurity assessment is always the first step. While this can be a painful and time-consuming process, Zyston has a solution. Our CyberCAST security assessment offers minimal disruption to the organization at a very affordable price point, meaning you can reduce costs while shortening your time-to-value.
The CyberCAST security assessment results in a report, ready to share with senior executives. The report explains the maturity of the organization’s security posture in a business language they can easily comprehend, making it easy to get buy-in from leadership as they’ll understand the risk—and the value—right away.
As a client’s information security partner, Zyston can both execute the CyberCAST assessment and facilitate the communication of the CyberCAST assessment findings with the client’s leadership team.
For a limited time, Zyston is offering an introductory CyberCAST Snapshot. In just a few short minutes, you can establish your security program’s maturity and get a sense of how it compares to industry benchmarks.
Request your free CyberCAST Snapshot security assessment today.
About Zyston:
Zyston is a managed security service (MSSP & MDR/XDR) provider dedicated to providing businesses with a comprehensive range of MSSP & MDR end-to-end services required to build and operate a mature and cost-effective information security program. We combine consulting, staffing, and managed security services to provide the best cyber program management on the market today.
Zyston has offices in Dallas, TX, Atlanta, GA, Austin, TX, San Francisco, CA and Denver, CO. For more information, visit www.zyston.com.
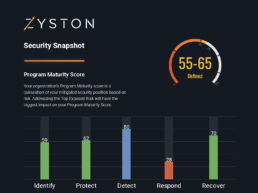
CyberCast Security Reporting
Security reporting that speaks business
Zyston CyberCAST brings the world of cybersecurity metrics up out of the weeds and into the hands of executive decision makers so nothing gets lost in translation. With CyberCAST, your organization gets clear visibility on security risks and also how your organization scores against your industry peers.
NIST Security Score
Get Your Security Score!




















